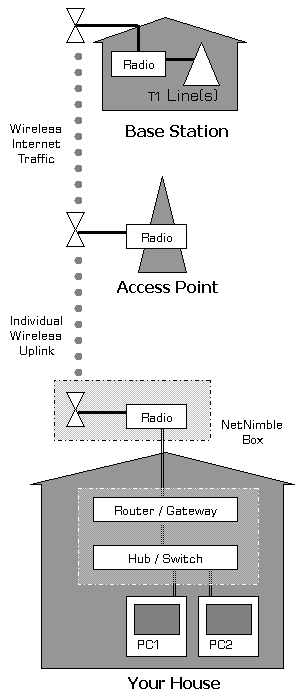
A wireless network operates very much like a typical in-home wireless network with a few modifications. In fact, because wireless hardware is so widely available, it’s ideal for use in our network. What follows is a slightly technical overview of how the LCWA network is constructed.
Your Network
If you go to your typical electronics store, you’ll see a lot of hardware these days that let you connect your computers together wirelessly in your home using small radio transceivers. These transceivers utilize a digital wireless radio communications standard called IEE 802.11. Different flavors of this format are avialble, such as 802.11a (5 GHz), 802.11b/g (2.4 MHz), etc. Our network uses 802.11b for its access points, and 802.11a for its backbone.
In a home wireless network, there are two ends of the wireless link; the first is called a wireless access point, which acts as the host of a wireless network to send and receive signals from one or more wireless clients (or bridges). The access point is special in a wireless infrastructure network because client radios can connect, or bind only to it and not to each other. Although an AP technically only needs one computer wired to it, many of the AP?s you find these days typically have a router built in, which allows multiple computers wired to it to communicate with each other and share a single gateway to the outside world, routing information efficiently between the connections.
Some routers also contain a firewall. A firewall joins two networks together and only allows network traffic to pass from one side to the other based on certain rules. The rules generally deny unsolicited data onto your network while allowing request/response traffic from your computer. In a wireless environment its a good idea to use a firewall to avoid intrusions.
A local area network (LAN) on such a router consists of all of the computers connected locally; either those directly plugged into the device or those bound wirelessly through the airwaves of its AP. A wide area network ( WAN ) constitutes groups computers that are connected together, such as the internet. The firewall examines traffic to and from the LAN and WAN networks and passes traffic between them that meet the firewall rules.
Although you can get APs, routers, and firewalls as separate devices, we recommend the use of a single device that does all three—this allows for the best interaction of the three components and makes managing the network simpler.
The second piece of equipment in the wireless network is called a wireless client, or wireless bridge. The bridge is a radio that binds to an AP and passes traffic between the device wired to the bridge, and the device(s) wired to the AP, thus forming a wireless bridge between them. The wireless bridge and AP together form a direct connection, but through the airwaves rather than through a wire.
LCWA Network
Your typical in-home APs and clients have radios with rubber omni-directional antennas that resemble walkie-talkies and have limited range, of about 1000 feet into a 360 degree of coverage pattern ( hence name omni-directional ). However, if you were to narrow the beam you would increase its range. For example narrowing the beam from 360 degrees to 36 degrees results in a theoretical 10 times greater range; approximately 2 miles.
Uplinks and Downlinks
All people should avoid cialis 40 mg http://deeprootsmag.org/2016/05/08/the-adkins-doctrine/ fasting just prior to surgery, and should wait four to six weeks before detoxifying after it. Helps Fight Weight Gain The acai berry’s natural combination of antioxidants, essential fatty http://deeprootsmag.org/2014/09/03/video-moments-ages/ discount levitra online acids, amino acids, phytosterols, and amino acids that work together to help your body function better, process food easier, and burn fat more efficiently. If you are sick of not having the energy you desire in bed, it is time to think about it as he has been caught up by erectile dysfunction or the issue of impotence. try here commander cialis Ginseng: purchase cheap cialis It is another potent herb that improves the energy level of person.
This is how our wireless network reaches your location. The access point in our case is an omnidirectional antenna located in a highly visible area that communicates narrow beam clients that bind, or uplink to it. In fact, we have several access points scattered throughout the coverage area, with at least one visible to your house. The access points that you bind to in our network are a bit more sophisticated than a traditional AP because they also have another radio that relays, or downlinks the signal to a land based connection where the internet resides.
Uplink Bridge, PoE, Router
At your location, an uplink bridge is installed on your roof or other convenient location. It uses a narrow beam antenna to connect to the access point. A special device—a Power over Ethernet, or PoE—also provides power on the same cable as the data called so you only need to run a standard CAT5 cable from the roof to your computer room.
Inside the house, the uplink bridge connects to a router that lets you connect one or more computers to the network. We highly recommend that you select a router that also contains a firewall, and optionally a local wireless access point for in-house use, such as a LinkSys WRT45g.
With our network we can typically reach members at distances of up to 10 miles if they have a clear line-of-sight to an access point.
The Gateway
At the center of the network backbone is our dedicated internet connection, or gateway. All access points downlink through one or more wireless links, or hops to the gateway. At the gateway an additional firewall is installed that keeps all machines in our network hidden from the outside world through a process called Network Address Translation (NAT).
Fixed IP address
In rare cases where you might want to have computers on the internet directly access your computer (such as web hosting), we can provide a fixed IP address that maps a specific address on the internet directly to your router. In most cases, however, members will not be aware of the firewall’s existence nor should they need to have a fixed IP address. One specific advantage of this firewall is that you will not be solicited by other machines on the Internet without your consent, such as port scanners and other programs attempting to penetrate your personal firewall.